OWASP 类别:MASVS-PLATFORM:平台互动
概览
“点按劫持”发生在 Android 应用中,是与点击劫持 Web 漏洞对等的攻击:恶意应用通过添加叠加层来遮盖界面的方式或通过其他方式,诱骗用户点击与安全相关的控件(确认按钮等)。在本页中,我们将对以下两种攻击变体加以区分:完全遮盖和部分遮盖。在完全遮盖攻击中,攻击者会为触摸区域添加叠加层;而在部分遮盖攻击中,触摸区域不会被遮盖。
影响
点按劫持攻击用于诱骗用户执行特定操作。具体影响取决于攻击者想要诱骗用户执行的操作。
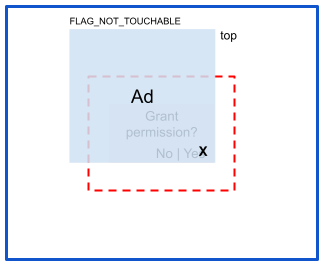
风险:完全遮盖
在完全遮盖攻击中,攻击者会为触摸区域添加叠加层,以便劫持触摸事件:
缓解措施
在代码中设置 View.setFilterTouchesWhenObscured(true) 可防止完全遮盖。这会屏蔽叠加层传递的触摸事件。如果您更喜欢采用声明式方法,还可以在布局文件中为要保护的 View 对象添加 android:filterTouchesWhenObscured="true"。
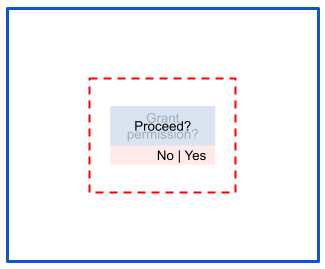
风险:部分遮盖
在部分遮盖攻击中,触摸区域不会受到遮盖:
缓解措施
通过手动忽略带有 FLAG_WINDOW_IS_PARTIALLY_OBSCURED 标志的触摸事件,可以缓解部分遮盖问题。这种情景没有默认的保护机制。
潜在注意事项:这种缓解措施可能会对没有问题的应用造成干扰。在某些情况下,您无法发布此类修复程序,因为如果部分遮盖是由没有问题的应用导致的,这会对用户体验产生负面影响。
具体风险
本部分将汇总符合以下条件的风险:需要采用非标准的缓解策略,或原本已在特定 SDK 级别得到缓解,而为了提供完整信息才列在此处。
风险:android.Manifest.permission.SYSTEM_ALERT_WINDOW
SYSTEM_ALERT_WINDOW 权限允许应用创建在所有应用上层显示的窗口。
缓解措施
较新版本的 Android 引入了几种缓解措施,其中包括:
- 在 Android 6(API 级别 23)及更高版本中,用户必须明确向应用授予创建叠加窗口的权限。
- 在 Android 12(API 级别 31)及更高版本中,应用可以将
true传递到Window.setHideOverlayWindows()。
风险:自定义消息框
攻击者可以使用 Toast.setView() 自定义消息框的外观。在 Android 10(API 级别 29)及更低版本中,恶意应用可能会从后台启动此类消息框。
缓解措施
如果应用以 Android 11(API 级别 30)或更高版本为目标平台,系统会屏蔽后台自定义消息框。不过,在某些情况下,可以通过“消息框爆发”的手段规避这种缓解措施:攻击者趁应用位于前台时将多个消息框列入队列,这样一来,即使应用进入后台,这些消息框也会继续启动。
从 Android 12(API 级别 31)开始,后台消息框攻击和消息框爆发攻击已彻底得到缓解。
风险:activity sandwich
如果恶意应用成功诱使用户打开它,它仍然可以启动受害应用中的 activity,随后为其叠加自己的 activity,从而形成“activity sandwich”,并实现部分遮盖攻击。
缓解措施
查看适用于部分遮盖攻击的常规缓解措施。为加强防御,请确保您不会导出原本不需要导出的 activity,以防止攻击者对其做 sandwich 处理。
资源
为您推荐
- 注意:当 JavaScript 处于关闭状态时,系统会显示链接文字
- android:exported
- # 密钥管理 {:#key-management}
- 直接从 APK 运行嵌入式 DEX 代码
